11-07-12 | Blog Post

Trustwave’s 2012 Global Security Report produced several key findings on data breaches and security issues across many industries. Here are a few of the findings, with resources to help remedy them:
Customer records made up 89 percent of all breached data investigated.
Companies that accept, store, process and/or transmit credit cardholder data must meet PCI DSS compliance. This includes companies that offer Software-as-a-Service (Saas) for e-commerce and billing payment solutions. Although the PCI standard has been around for years, not all companies are educated in how to build a secure environment and protect cardholder data under the 12 requirements, leading to a large amount of breached customer record data.
Find out more about PCI DSS compliance to cut down on your risk of contributing to overall breached data:
More than a third of all 2011 breaches were found in the franchise industry.
For every franchise, there is a weak link. Even though corporate franchise chains require franchisees to maintain standard levels of point-of-sale (POS) system security, not all franchisees comply. Hackers know this, and target the smaller stores that are linked to the corporate network.
The Subway franchise suffered a breach resulting in $3 million fraudulent charges from more than 150 of its locations. Hackers were able to access their POS systems by running a targeted port scan of blocks of IP address to detect systems that used a certain type of remote desktop access software – while PCI DSS requires the use of two-factor authentication for remote access, a few Subway locations did not have this in place. Many locations also did not use point-to-point encryption and downloaded remote desktop software online, disregarding corporate’s security guidelines.
Barnes and Noble was also hit by a data breach that targeted their cash register customer keypads across 10 states in several different in-store locations. Read more about the cases in Franchise Point-of-Sale (POS) Systems Targeted in Nationwide PCI Data Breach.
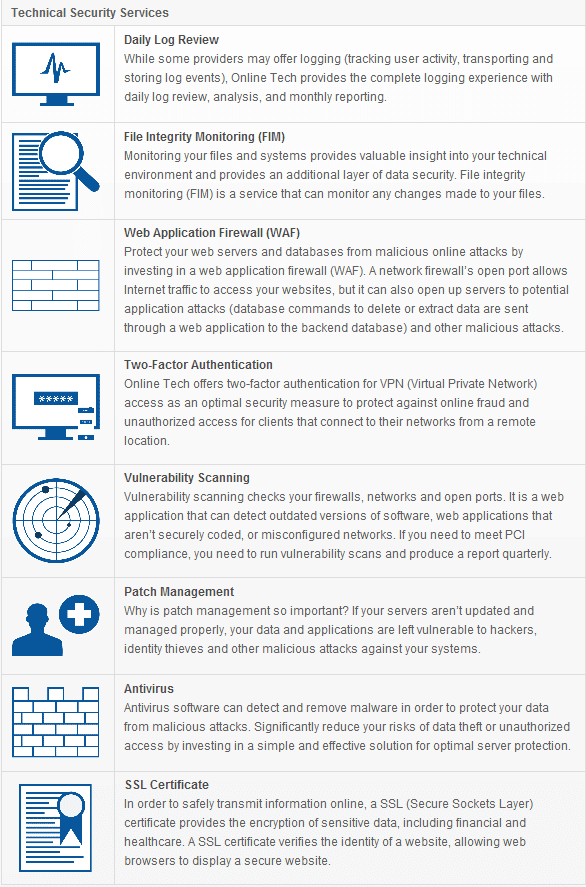
Find out which Technical Security services you can implement to create many different layers of security around your data and applications, and meet PCI DSS compliance:
Third-parties were responsible for introducing security deficiencies in 76 percent of all breaches.
In accordance with the litany of breaches seen in the healthcare industry, third-party service providers have been the root cause of many a data breach, due to either mishandling of sensitive data, stolen or lost portable media, and issues that can be traced back to poor or lack of security-trained staff.
How can you protect your organization and still make the best use of third-party services? Ask your PCI hosting or HIPAA hosting provider about:
Audits and Reports
What kind of audits has your data center and hosting provider invested in, and when was the last date of their audit report? What kind of measurements and standards do these audits follow? Are they willing to disclose a copy of their reports on compliance? From SOC 2 to HIPAA, do your due diligence to ensure they’re familiar with your industry’s requirements. Read our Data Center Standards Cheat Sheet for a quick and dirty summary of each audit.

Gain insight into your third-party provider’s culture of security by viewing their documented policies and procedures that may cover anything from password standards to data handling after service termination. How a provider handles breach notification and their disaster recovery plan can also affect your company in a worst case scenario. Get familiar with the scope of their policies.

Regular employee training is key to keeping a secure environment. As reported in the blog, Michigan Cyber Initiative Reports ‘People’ As Weakest Link in IT Security, untrained or careless staff can also be traced back as the root cause of a data breach. Check the last dates of your service provider’s employee training, and inquire about hiring policies to ensure your data is in safe hands.
Data in-transit were targeted in 62.5 percent of all breaches.
Encryption of data at rest (in storage and on servers) and in transit is important to satisfy PCI and HIPAA requirements, and is vital to secure information exchange. Follow the NIST (National Institute of Standards and Technology) Special Publication 800-111, Guide to Storage Encryption Technologies for End User Devices standards for encryption. Read more about data protection in our HIPAA Compliant Hosting white paper, and our PCI Compliant Hosting white paper.
Antivirus software detected less than 12 percent of targeted malware found in the study.
Antivirus software alone isn’t a proper defense against malware and other attacks on your systems. Read more about other technical security defenses you can use in conjunction with antivirus software.
SQL injection is the top method for web-based attacks for the fourth year in a row.
Protect your web servers and databases from malicious online attacks by investing in a web application firewall (WAF). A network firewall’s open port allows Internet traffic to access your websites, but it can also open up servers to potential application attacks (database commands to delete or extract data are sent through a web application to the backend database) and other malicious attacks.

A WAF can protect your servers more than a traditional IPS/IDS (Intrustion Protection/Detection System) can by detecting and preventing SQL injections. Find out more about Web Application Firewalls.
References:
Trustwave 2012 Global Security Report

Trustwave’s 2012 Global Security Report produced several key findings on data breaches and security issues across many industries. Here are a few of the findings, with resources to help remedy them:
Customer records made up 89 percent of all breached data investigated.
Companies that accept, store, process and/or transmit credit cardholder data must meet PCI DSS compliance. This includes companies that offer Software-as-a-Service (Saas) for e-commerce and billing payment solutions. Although the PCI standard has been around for years, not all companies are educated in how to build a secure environment and protect cardholder data under the 12 requirements, leading to a large amount of breached customer record data.
Find out more about PCI DSS compliance to cut down on your risk of contributing to overall breached data:
More than a third of all 2011 breaches were found in the franchise industry.
For every franchise, there is a weak link. Even though corporate franchise chains require franchisees to maintain standard levels of point-of-sale (POS) system security, not all franchisees comply. Hackers know this, and target the smaller stores that are linked to the corporate network.
The Subway franchise suffered a breach resulting in $3 million fraudulent charges from more than 150 of its locations. Hackers were able to access their POS systems by running a targeted port scan of blocks of IP address to detect systems that used a certain type of remote desktop access software – while PCI DSS requires the use of two-factor authentication for remote access, a few Subway locations did not have this in place. Many locations also did not use point-to-point encryption and downloaded remote desktop software online, disregarding corporate’s security guidelines.
Barnes and Noble was also hit by a data breach that targeted their cash register customer keypads across 10 states in several different in-store locations. Read more about the cases in Franchise Point-of-Sale (POS) Systems Targeted in Nationwide PCI Data Breach.
Find out which Technical Security services you can implement to create many different layers of security around your data and applications, and meet PCI DSS compliance:
Third-parties were responsible for introducing security deficiencies in 76 percent of all breaches.
In accordance with the litany of breaches seen in the healthcare industry, third-party service providers have been the root cause of many a data breach, due to either mishandling of sensitive data, stolen or lost portable media, and issues that can be traced back to poor or lack of security-trained staff.
How can you protect your organization and still make the best use of third-party services? Ask your PCI hosting or HIPAA hosting provider about:
Audits and Reports
What kind of audits has your data center and hosting provider invested in, and when was the last date of their audit report? What kind of measurements and standards do these audits follow? Are they willing to disclose a copy of their reports on compliance? From SOC 2 to HIPAA, do your due diligence to ensure they’re familiar with your industry’s requirements. Read our Data Center Standards Cheat Sheet for a quick and dirty summary of each audit.

Gain insight into your third-party provider’s culture of security by viewing their documented policies and procedures that may cover anything from password standards to data handling after service termination. How a provider handles breach notification and their disaster recovery plan can also affect your company in a worst case scenario. Get familiar with the scope of their policies.

Regular employee training is key to keeping a secure environment. As reported in the blog, Michigan Cyber Initiative Reports ‘People’ As Weakest Link in IT Security, untrained or careless staff can also be traced back as the root cause of a data breach. Check the last dates of your service provider’s employee training, and inquire about hiring policies to ensure your data is in safe hands.
Data in-transit were targeted in 62.5 percent of all breaches.
Encryption of data at rest (in storage and on servers) and in transit is important to satisfy PCI and HIPAA requirements, and is vital to secure information exchange. Follow the NIST (National Institute of Standards and Technology) Special Publication 800-111, Guide to Storage Encryption Technologies for End User Devices standards for encryption. Read more about data protection in our HIPAA Compliant Hosting white paper, and our PCI Compliant Hosting white paper.
Antivirus software detected less than 12 percent of targeted malware found in the study.
Antivirus software alone isn’t a proper defense against malware and other attacks on your systems. Read more about other technical security defenses you can use in conjunction with antivirus software.
SQL injection is the top method for web-based attacks for the fourth year in a row.
Protect your web servers and databases from malicious online attacks by investing in a web application firewall (WAF). A network firewall’s open port allows Internet traffic to access your websites, but it can also open up servers to potential application attacks (database commands to delete or extract data are sent through a web application to the backend database) and other malicious attacks.

A WAF can protect your servers more than a traditional IPS/IDS (Intrustion Protection/Detection System) can by detecting and preventing SQL injections. Find out more about Web Application Firewalls.
References:
Trustwave 2012 Global Security Report