04-05-12 | Blog Post
A recent study by KPMG on federal cloud adoption reveals main drivers, demotivators and tips for what to look for in a cloud hosting provider for both private and the public sector. The study reported findings on governments, citizens, cloud service providers and IT leaders.

Security is a major concern when it comes to the cloud, but certification could help – while 47 percent of government respondents cite security as their most significant concern, nearly 80 percent claimed they would be more confident if cloud services were certified by a government entity.
Cost is the main driver for both government and the private sector to move to the cloud, with 73% and 75% respectively claiming it was necessary to realize cost reductions and savings in order to move to a cloud environment.
But how significant would those savings need to be in order to make the transition? At 43%, the private sector only needs 1-10% reduction in IT or non-IT costs to switch over, while the public sector appears to be confused, with 29% claiming they didn’t know what percent reduction in budgetary costs they needed in order to make a cloud decision.
In addition to cost, technical drivers, such as flexibility, scalability, simplicity, security and advanced technology, were ranked as either important or extremely important by 79% of government respondents, and likewise by the private sector.
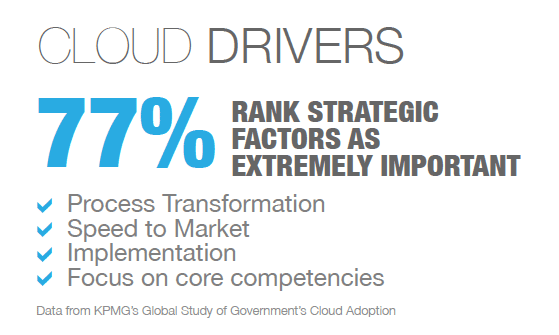
Strategic factors, such as process transformation, linkage to business/organization partners, speed to market/implementation and a focus on core competencies were ranked as important or extremely important by 77% of private businesses. This extends the benefits of cloud computing to a broader business perspective as companies prepare for long-term growth and reorganize priorities in order to realize increased efficiency.
What does a government (and as should any company concerned with security) look for in a cloud provider? Dave McClure, Associate Administrator of the Office of Citizen Services and Innovative Technologies at the U.S. General Services Administration (GSA) lists a few:
The study provides some excellent closing insights/tips for a range of professionals, including government leaders, government IT professionals, cloud vendors and more. Recognizing the new security challenges presented by the cloud, the study advises government leaders (or business leaders) to find an effective and accurate way to audit several areas under the cloud, including:
The study urges professionals to ask the following questions as they navigate the cloud vendor selection process:
For more on the cloud, check out our comprehensive Cloud Wiki and our informative Cloud Computing E-Tips.
References:
KPMG Global Study of Governments’ Adoption of the Cloud (PDF)
A recent study by KPMG on federal cloud adoption reveals main drivers, demotivators and tips for what to look for in a cloud hosting provider for both private and the public sector. The study reported findings on governments, citizens, cloud service providers and IT leaders.

Security is a major concern when it comes to the cloud, but certification could help – while 47 percent of government respondents cite security as their most significant concern, nearly 80 percent claimed they would be more confident if cloud services were certified by a government entity.
Cost is the main driver for both government and the private sector to move to the cloud, with 73% and 75% respectively claiming it was necessary to realize cost reductions and savings in order to move to a cloud environment.
But how significant would those savings need to be in order to make the transition? At 43%, the private sector only needs 1-10% reduction in IT or non-IT costs to switch over, while the public sector appears to be confused, with 29% claiming they didn’t know what percent reduction in budgetary costs they needed in order to make a cloud decision.
In addition to cost, technical drivers, such as flexibility, scalability, simplicity, security and advanced technology, were ranked as either important or extremely important by 79% of government respondents, and likewise by the private sector.

Strategic factors, such as process transformation, linkage to business/organization partners, speed to market/implementation and a focus on core competencies were ranked as important or extremely important by 77% of private businesses. This extends the benefits of cloud computing to a broader business perspective as companies prepare for long-term growth and reorganize priorities in order to realize increased efficiency.
What does a government (and as should any company concerned with security) look for in a cloud provider? Dave McClure, Associate Administrator of the Office of Citizen Services and Innovative Technologies at the U.S. General Services Administration (GSA) lists a few:
The study provides some excellent closing insights/tips for a range of professionals, including government leaders, government IT professionals, cloud vendors and more. Recognizing the new security challenges presented by the cloud, the study advises government leaders (or business leaders) to find an effective and accurate way to audit several areas under the cloud, including:
The study urges professionals to ask the following questions as they navigate the cloud vendor selection process:
For more on the cloud, check out our blog.
References:
KPMG Global Study of Governments’ Adoption of the Cloud (PDF)